Fortra Vulnerability Management
Fortra Vulnerability Management (formerly Frontline VM), is the industry’s most comprehensive, accurate, and easy-to-use SaaS vulnerability management solution—bar none. Using proprietary scanning technology, it performs comprehensive security assessments and helps prioritize and track the results, making remediation planning and management more efficient and effective.
Meet Fortra VM
Fortra Vulnerability Management is more than just a network vulnerability scanner or vulnerability assessment. It's a proactive, risk-based vulnerability and threat management solution that is a vital part of any cyber risk management program. Its robust features set it apart from other VM solutions, providing vital security information in a centralized, easily understood format so you can protect your business-critical assets efficiently and effectively.
The Preferred Solution for
Risk-Based Vulnerability Management Among G2 Users.





Don't just take our word for it, see for yourself.
Click here to read G2 reviews >
Best Practices in Vulnerability Management
More than ever, cyber attackers are looking for vulnerabilities they can exploit in a company’s network. So having a VM solution in place is critical.
A network security program is far more than just a vulnerability assessment, vulnerability scanner, or patch management. The best network protection comes from using ongoing process like VM scans that regularly identify, evaluate, report, and prioritize vulnerabilities in systems and software.
Fortra VM uses rich data and superior technology to arm your team with the most powerful tools and easy-to-use vulnerability management and threat assessment solutions on the market. Our cloud-native, SaaS platform makes it easy to get up and running in hours rather than days.
Extensive, easy-to-use capabilities include:
Vulnerability Scanning
Compliance Auditing
Smart Labels
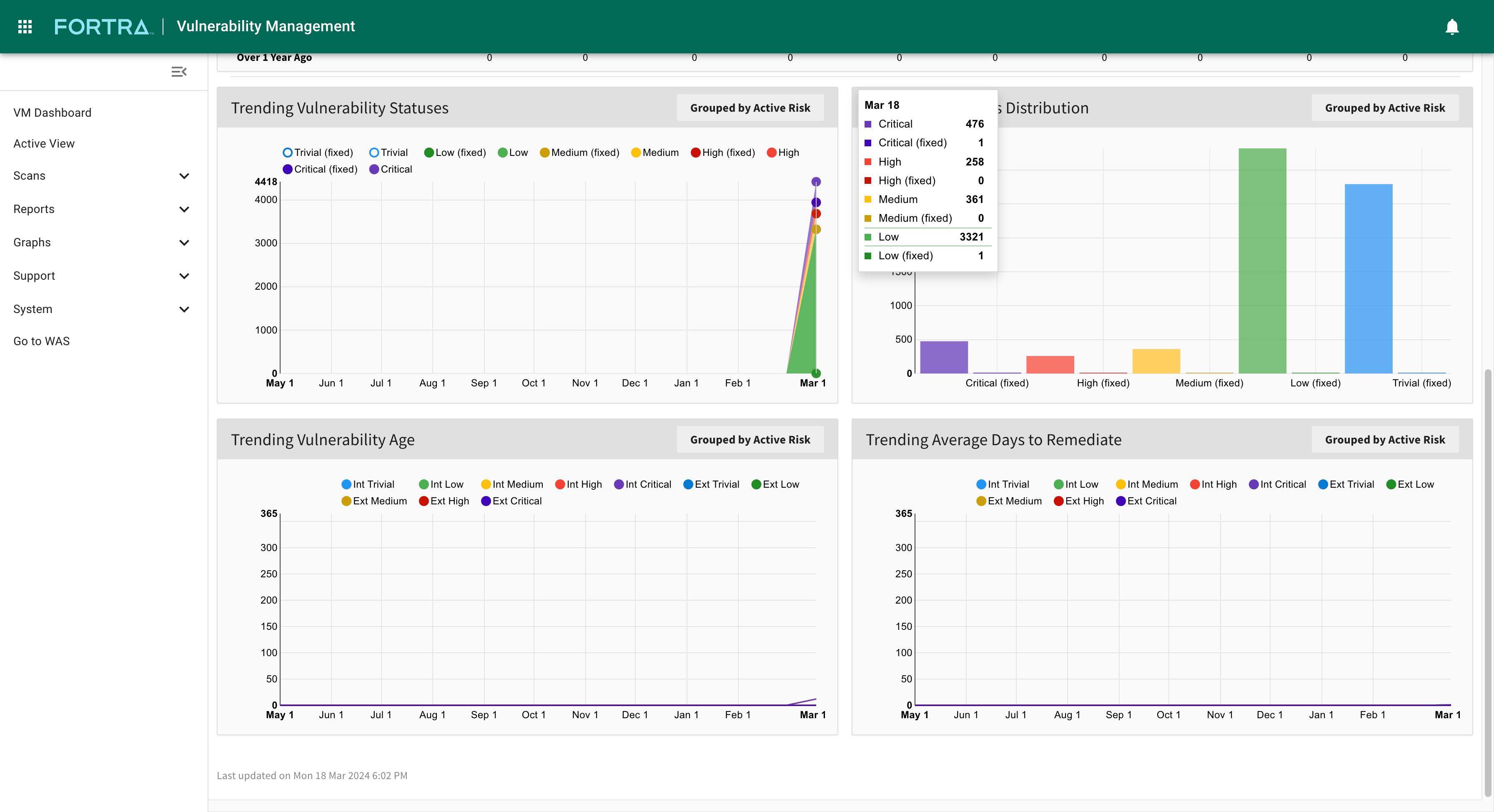
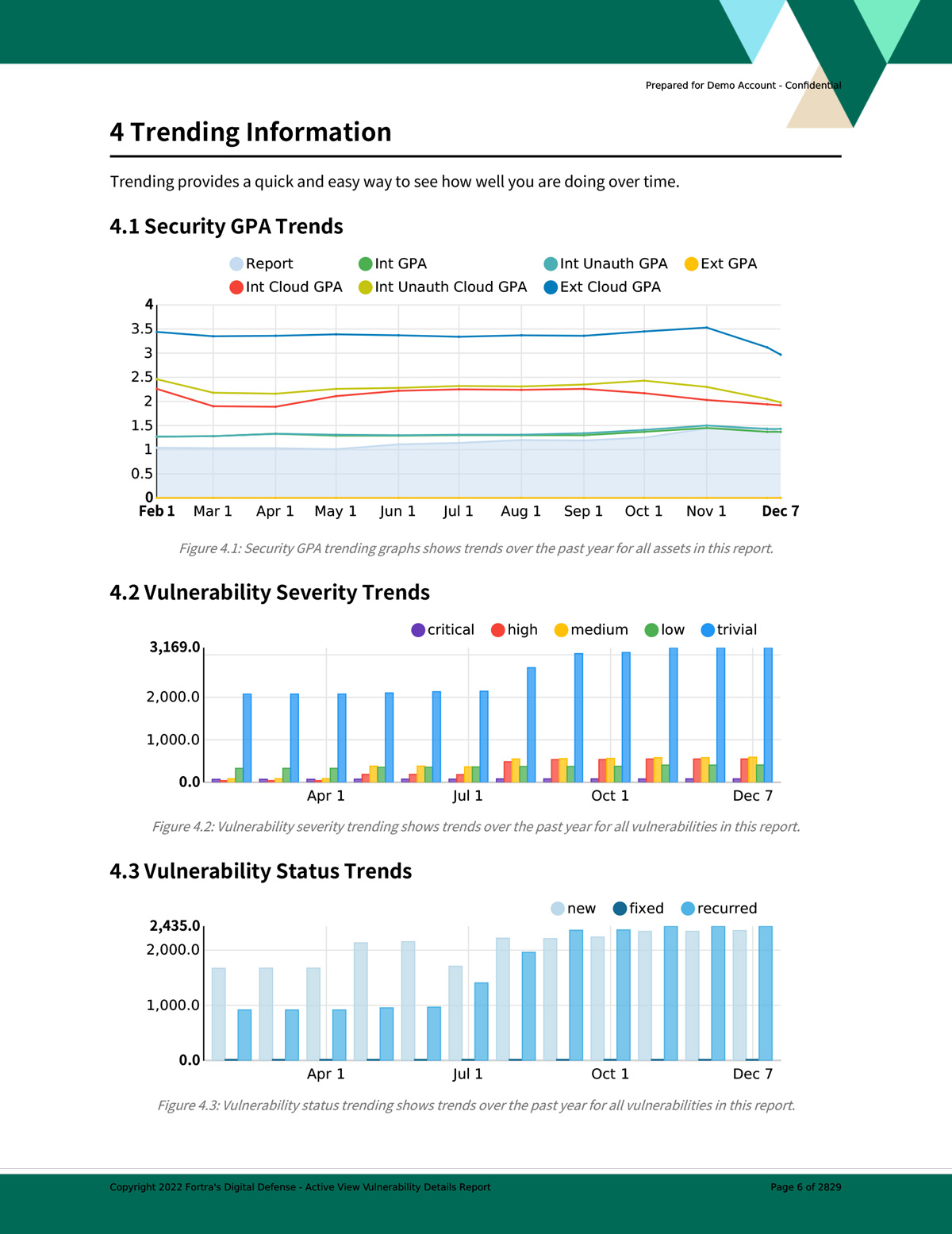
Trending
Network Endpoint Correlation
Role-Based Access Control & Data Segmentation
Customizable Reports
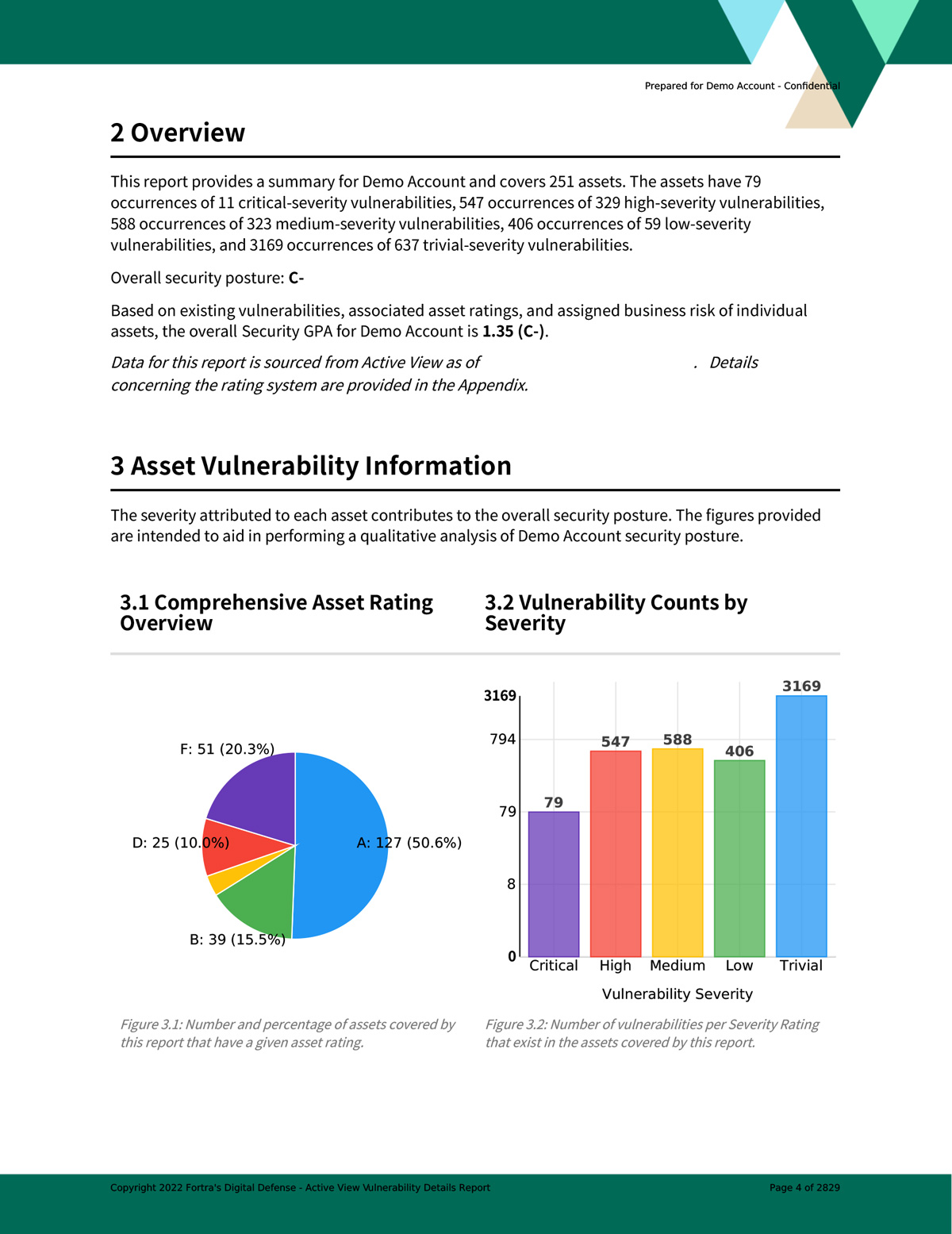
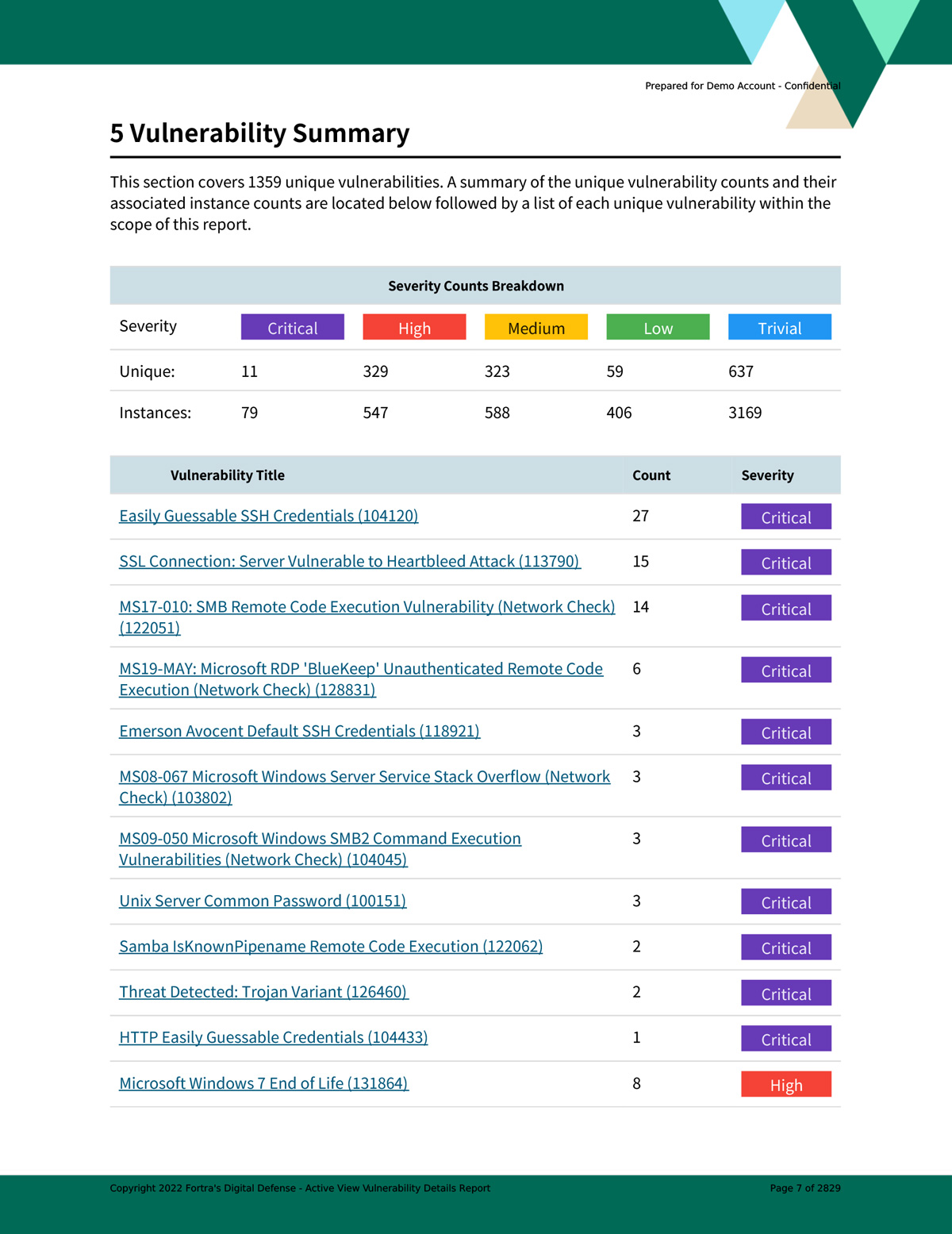
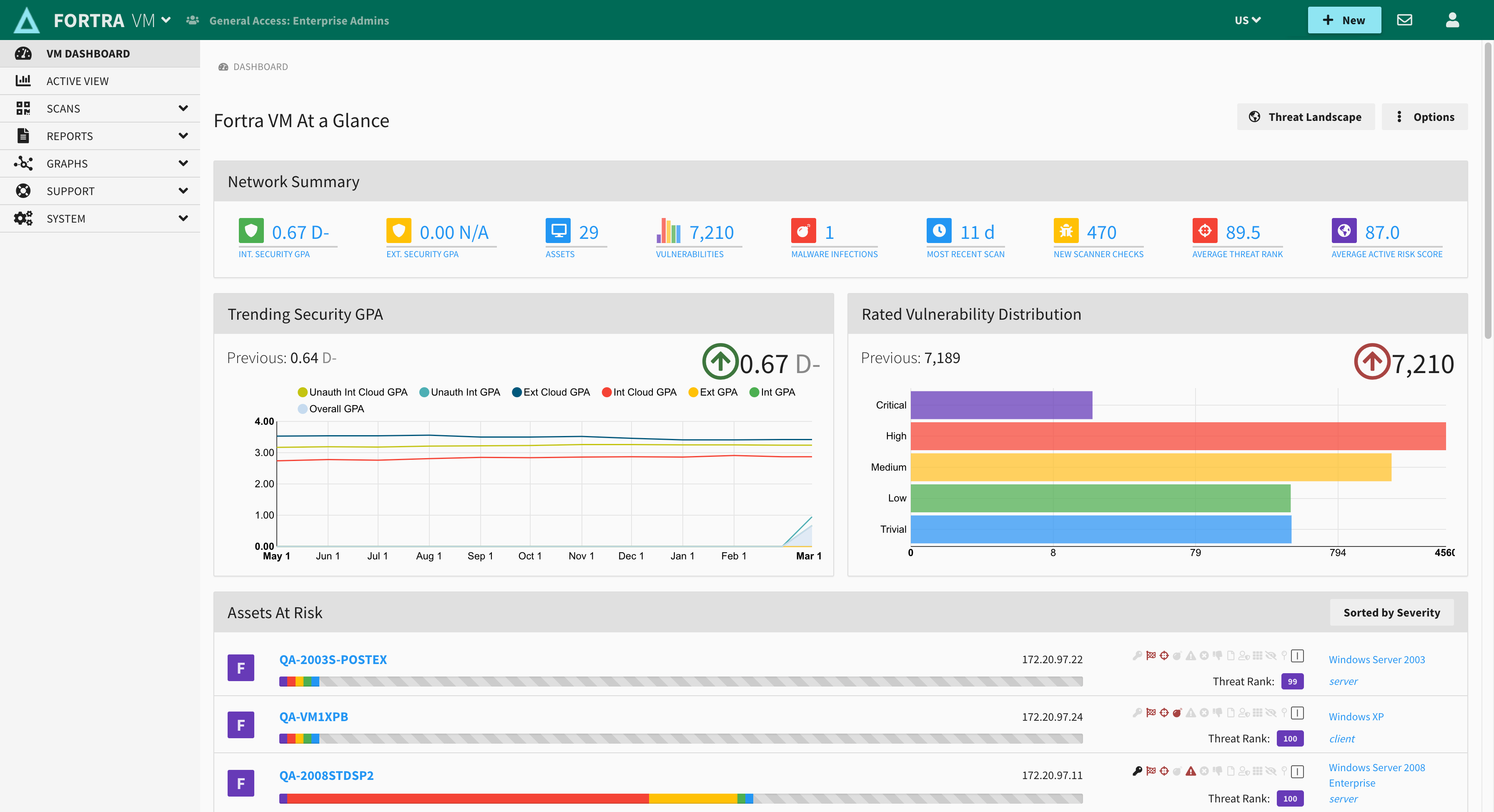
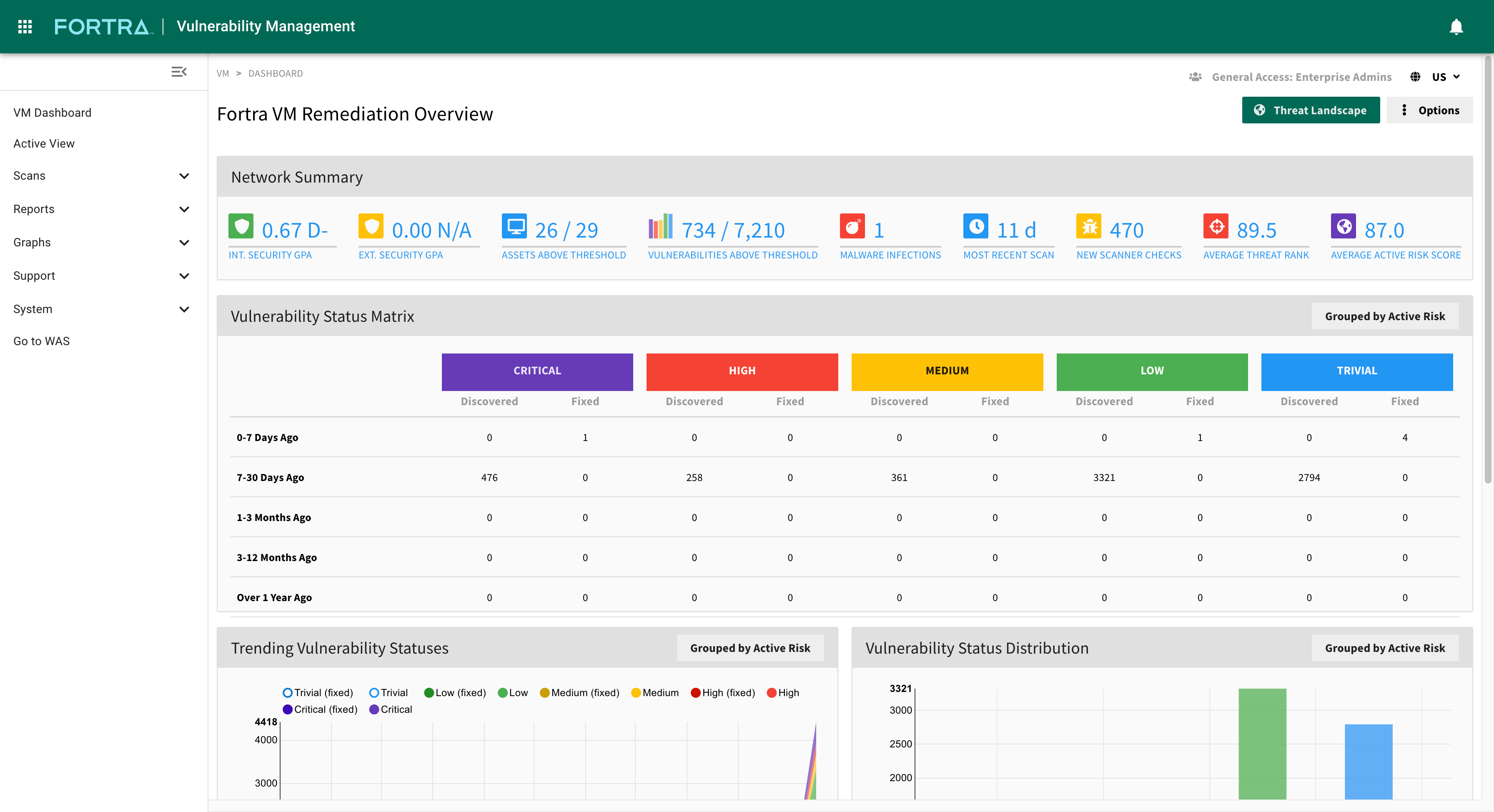
Create asset-specific vulnerability and patch management reports based on powerful filtering options tailored to your audience or compliance target.
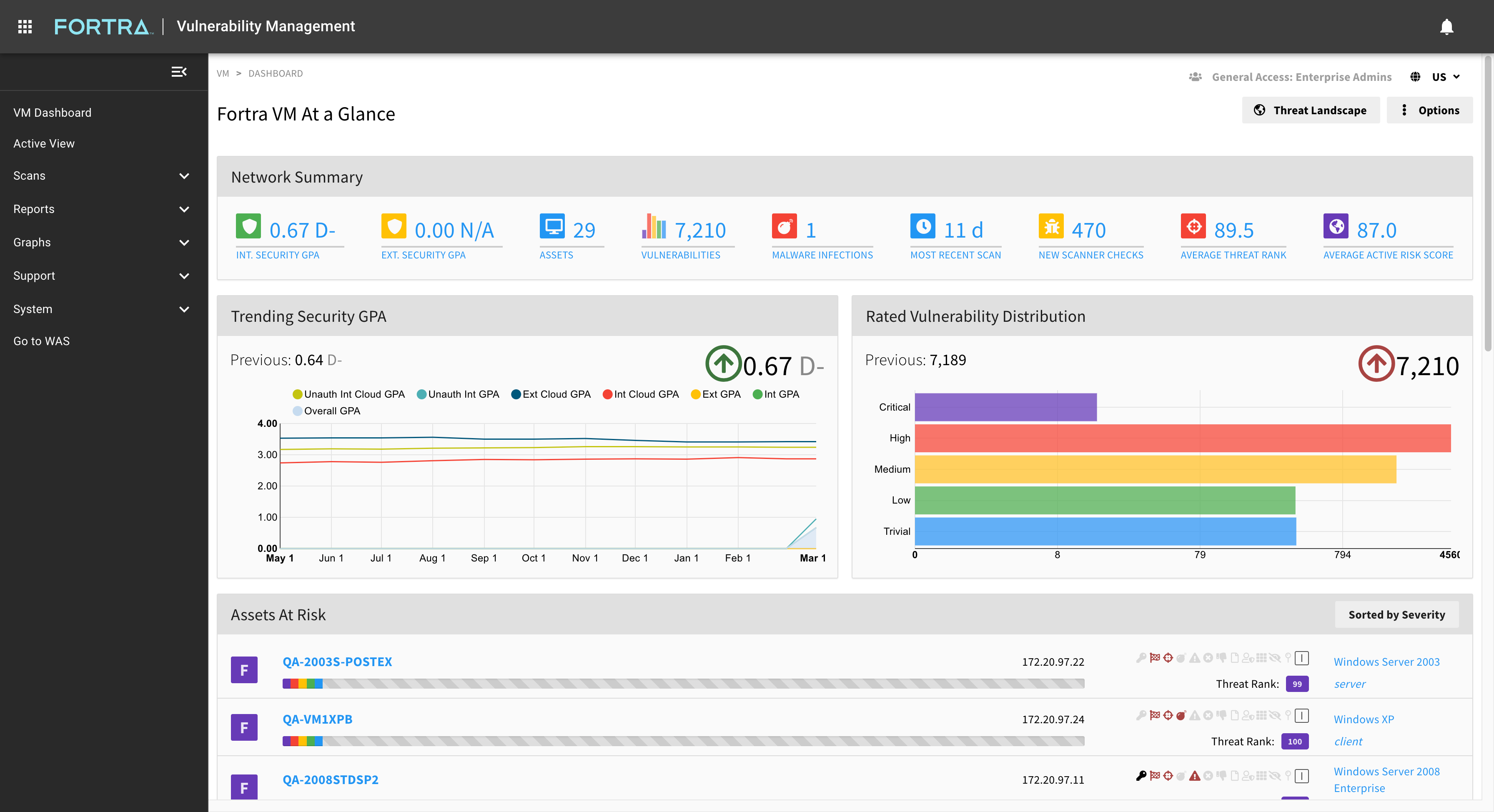
Threat ranking identifies the highest priority threats specifically for your company's security details. A threat rank score combines vulnerability severity, asset exposure, and asset criticality to create an easy to assess GPA security rating for your organization's risk.
Customizable reporting helps you track the metrics that are more important to your organization’s security efforts. Measure progress and track security remediation efforts in your threat landscape. Analyze and report on continuing security trends based on asset and vulnerability metrics.
Get a Free Trial
Try it for yourself, see how Fortra VM can help your organization prioritize the most harmful vulnerabilities based on your specific industry.
Fortra VM Features
Threat Landscape
Security GPA®
Network Map
Connect API
Peer Insight
How to Get Fortra VM
Fortra VM is an on-demand service on an annual subscription plan through our convenient, time-saving, hassle-free SaaS service subscriptions.
Leverage the power of our vulnerability management software and benefit from an affordable solution with continuous monitoring that enhances your overall security posture.
At Digital Defense, one size does not fit all. Whether you are a large organization with a fully staffed security team or a small business with limited time and resources, we offer flexible vulnerability management options to meet your needs. Our subscriptions are available as client-managed or Digital Defense-managed options at a frequency level that meets your needs, while ensuring optimal security.
We will help you ensure your vulnerability management and threat assessment program is targeted, effective and achievable.
GET A QUOTECLOUD SUBSCRIPTIONS
Elevate Your Defenses with Offensive Security Product Bundles
Did you know that Fortra VM can be coupled with industry-leading offensive security solutions like Core Impact and Cobalt Strike? By bundling products, you can customize your security tech stack to match your organization's distinct requirements all at a discounted rate.
Technology Partner Integrations
Fortra VM can integrate our patented solutions with our security technology partners.
These include leading SIEM, endpoint, SOAR, incident response, GRC, and network security solutions.




TAKE THE NEXT STEP
GET FRONTLINE VM, A ROBUST, IN-DEPTH VULNERABILITY MANAGEMENT SOLUTION THAT'S FLEXIBLE AND EASY-TO-USE.
Copyright © Fortra, LLC and its group of companies. Fortra™, the Fortra™ logos, and other identified marks are proprietary trademarks of Fortra, LLC. | Privacy Policy | Cookie Policy | Sitemap