What is Offensive Security?
Offensive security is the proactive approach to securing networks and systems from attacks by actively seeking out vulnerabilities and weaknesses. This involves simulating real-world attacks and attempting to penetrate systems, networks, and applications to identify security flaws. This approach aims to identify and remediate security weaknesses before malicious actors can exploit them.
An example of offensive security is the use of ethical hackers and professional security testers who mimic cyberattacks to identify potential weaknesses and improve an organization’s overall security posture. The shift towards offensive security is becoming increasingly important as organizations move towards a proactive security approach and away from reactively responding to attacks as they arise.
Offensive vs. Defensive Cybersecurity
Offensive and defensive cybersecurity both play important roles in protecting networks, systems, and data.
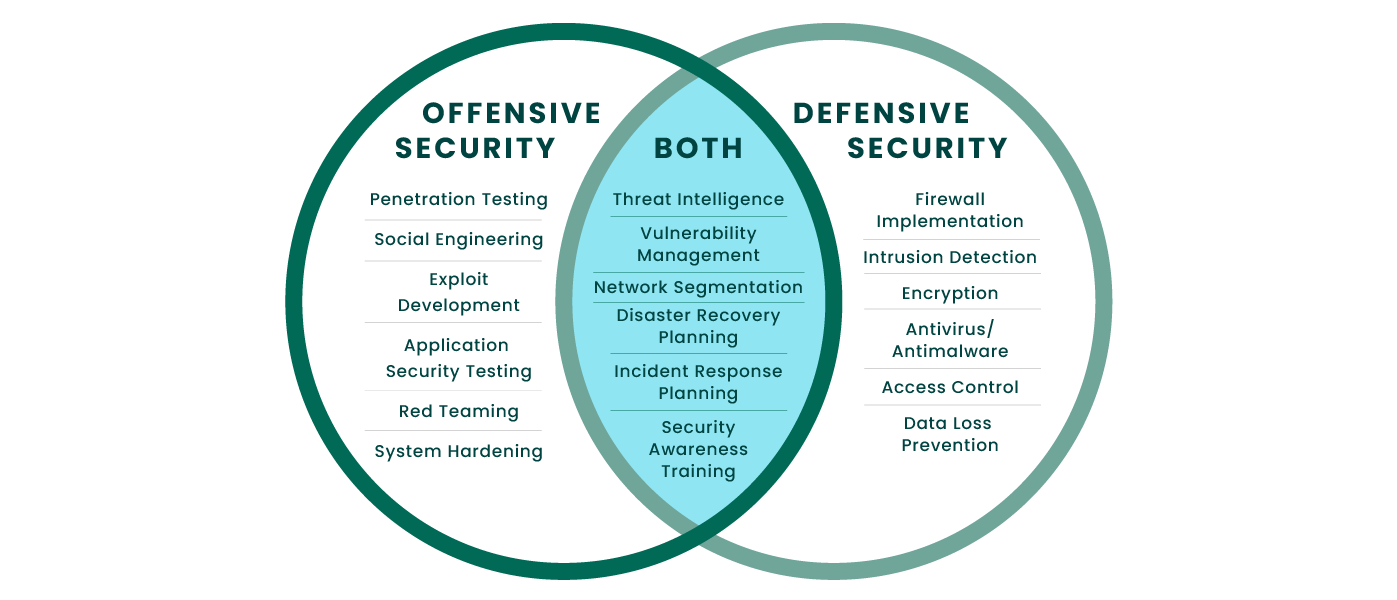
Offensive Security
Offensive security is focused on finding vulnerabilities and weaknesses in systems and networks through simulated attacks. This includes techniques such as penetration testing, red teaming, social engineering, and exploit development.
The goal of offensive security is to identify security gaps and potential attack vectors before malicious actors can exploit them.
Both
Both offensive and defensive security share the common goal of maintaining the security and integrity of systems and data. This is achieved through the use of threat intelligence, vulnerability management, advanced testing, network segmentation, disaster recovery planning, incident response planning, security awareness training, and other security best practices.
The combination of offensive and defensive security helps organizations build a comprehensive security strategy and reduce the overall risk of a successful cyber attack.
Defensive Security
Defensive security is focused on deflecting and detecting security breaches. This includes implementing security measures such as firewalls, intrusion detection systems, encryption, and antivirus/antimalware solutions.
The goal of defensive security is to defend known attack vectors and minimize damage if a breach does occur.
Empower Your Workforce
Discover how to equip your team with the skills needed to proactively identify and mitigate security weaknesses before they become critical issues.
Creating Effective Offensive Security Operations
Effective offensive security involves creating a repeatable strategy that can be employed for various projects. The following steps ensure that each engagement effectively targets required areas and can generate actionable findings:
- Defining the scope of the project: It is crucial to determine what the team hopes to learn through the engagement as well as which systems, networks, and applications they will be testing. This helps to ensure that everyone is on the same page and that all objectives are clearly defined.
- Gathering intelligence: This involves researching the target systems and gathering as much information as possible about them, including their architecture, configurations, and vulnerabilities.
- Selecting the right tools: The team must have access to the right offensive security tools and technologies to perform their tasks effectively. These may include penetration testing suites, vulnerability scanners, simulation solutions, command and control (C2) frameworks, and exploitation tools, among others.
- Conducting Engagements: Depending on the engagement type, teams are either looking to gain control of high-value data (red teaming) or determine the full extent of vulnerabilities (pen testing). Testers use offensive techniques while attempting to penetrate systems and networks to assess weaknesses and the extent of the risk.
- Reporting and remediation: Finally, the team should provide a report detailing their findings. The appropriate stakeholders should review and act upon the information to ensure that the identified weaknesses are remediated. The quality of these reports is crucial to optimizing team resources. Findings for endpoints must be correlated with hostnames to ensure proper host identification.
By following these steps, organizations give teams the scope and direction to create an effective engagement while allowing them the freedom to creatively implement offensive security tactics. Using this approach, engagements can more effectively discover exploitable vulnerabilities, allowing for faster time to remediation and improved security posture.
Offensive Security Solutions and Services
Offensive security solutions and services aim to identify and mitigate security risks by simulating real-world attack scenarios. These solutions and services are designed to help organizations understand their security posture, identify potential weaknesses and vulnerabilities, and implement best practices for remediation. Some commonly used offensive security solutions and services include penetration testing, red teaming, and vulnerability management programs.
These solutions and services can be tailored to meet an organization’s specific needs, whether it’s a small business, a large enterprise, or a government agency. By utilizing offensive security solutions and services, organizations can minimize the risk of a successful cyberattack.
Penetration Testing
Offensive security penetration testing, also known as pen testing, is a form of security testing that is used to evaluate the security of a system, network, or application. The goal of penetration testing is to exploit vulnerabilities in target systems and assess the level of risk for a successful attack. Penetration testers use various techniques, including manual and automated testing methods, to simulate real-world attack scenarios and evaluate the target system’s ability to resist attack.
Penetration testing is an essential component of a comprehensive security program, as it provides organizations with valuable insights into the effectiveness of their security measures. By verifying weaknesses, penetration testing helps organizations prioritize their security efforts and make informed decisions about their security investments. In addition, penetration testing allows organizations to validate their compliance with regulatory and industry standards and to demonstrate due diligence to stakeholders. Whether an organization is looking to protect sensitive data, maintain the availability of critical systems, or simply enhance its overall security posture, penetration testing can provide valuable information and support.

Red Teaming
Red teaming is a form of offensive security that involves simulating real-world attack scenarios to test an organization’s security posture. The goal of red teaming is to test for vulnerabilities and weaknesses and provide recommendations for remediation. Red teaming exercises are typically performed by highly skilled security professionals who use a combination of technical and non-technical techniques as well as red team tools and software to simulate the methods used by real-world attackers. This provides organizations with a realistic assessment of their security posture and helps them to prioritize their security efforts.
Red teaming is becoming increasingly important in today’s threat landscape, where attackers constantly evolve their techniques and attack surfaces continue to expand. Using skilled security testing personnel and offensive security tooling for red teams, organizations can find security gaps before they can be exploited by real-world attackers. Additionally, red teaming allows organizations to validate the effectiveness of their defensive security measures and to identify areas for improvement. In short, red teaming provides organizations with a proactive approach to security, allowing them to stay ahead of the threat and to better protect their critical assets.
Vulnerability Management
Vulnerability management is an ongoing process of identifying, assessing, and prioritizing vulnerabilities in a system, network, or application. The goal of vulnerability management is to reduce the risk of a security breach by identifying vulnerabilities before attackers can exploit them. This is accomplished through a combination of processes, including vulnerability scanning, threat intelligence analysis, and risk assessment.
A vulnerability management program helps organizations implement a structured and systematic approach to vulnerability management. This program typically includes regular vulnerability scans, regular patching and remediation activities, and the development of a comprehensive risk management strategy. The program also includes regular reporting and communication to stakeholders, including executives and senior managers, to help ensure that vulnerabilities are addressed promptly and effectively. By implementing the right vulnerability management program and solution, organizations can reduce the risk of a security breach and improve the overall security of their systems and data.
Benefits of Layering Solutions
Layering security solutions is a best practice in today’s threat landscape, providing organizations with a comprehensive and multi-faceted approach to security. By stacking security solutions, organizations can expand their reach and ensure they have complete coverage across all areas of their environment. A comprehensive security program might include a combination of vulnerability management, penetration testing, and red teaming. It’s helpful to identify vendors that offer interoperable versions of these solutions that share information and generate more insightful results. For example, the vulnerability management solution would identify vulnerabilities, share that information with pen testing software, and then penetration testing would validate the vulnerabilities’ exploitability. Similarly, pen testing and red teaming frameworks can use session passing, tunneling and share modules for extended testing capabilities.
Watch the video - Bundling Up: The Importance of Layering Offensive Security Solutions >
Featured Resources
Offensive Security Solutions and Services from Fortra
Be Proactive In Your Cybersecurity
Fortra helps you protect your business from cyberattacks and take a proactive approach to cybersecurity with bundled offensive security solutions. Stay ahead of potential threats, reduce console fatigue, and streamline your security efforts using interoperable solutions.
Copyright © Fortra, LLC and its group of companies. Fortra®, the Fortra® logos, and other identified marks are proprietary trademarks of Fortra, LLC. | Privacy Policy | Cookie Policy | Sitemap

