As part of our continual quest to ensure our Frontline vulnerability management and threat assessment solutions always meet the changing needs of modern cybersecurity, Digital Defense is upgrading subscriptions to make newer features available to all customers at no extra cost.
The newly included features span a comprehensive breadth of considerations and include Threat Landscape, Network Map, and CIS Benchmark Scanning. This covers much more than the basic vulnerability assessment; a deeper dive into the buildups of each feature illuminates the expansive capabilities and just how helpful these no-cost additions are. Digital Defense features hosted on Frontline.Cloud are built thoughtfully and purposefully, and the new rollouts pair intuitive use and performance with similar grace — happy news for experienced users, as well as those just starting out.
Prioritize Remediation with Threat Landscape
The word "feature" might not adequately describe Frontline Threat Landscape, in terms of its scale, value, and operability. It feels more like a platform, helping clients prioritize vulnerability remediation by providing research-driven insights into the threat types they face. Dynamic scores quantify vulnerability exploitation likelihood based on the threat activity observed in the wild.
Indeed, the inclusion of Frontline Threat Rank does just that, dynamically rating vulnerabilities on a 1-100 scale, with 1 indicating low risk and 100 being the highest active exploitation risk, using metrics extracted across a host of online resources that are updated daily. Some clients may already be familiar with Threat Rank, but now all users can take advantage of its threat-centric methodology to prioritize vulnerability remediation.
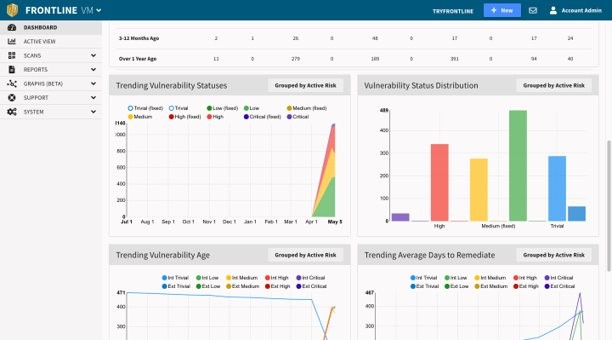
Threat Landscape is extremely well-armed. Its full configurability enables platform alignment with organizational risk postures, while reportability dashboards and functions enhance the user’s ability to leverage timely information on new threats and remediation. Further customization options allow users to specify settings for generating Active Risk Scores, , which help define and organization’s risk threshold. Active Risk Score combines Threat Rank, vulnerability severity, asset exposure, and asset criticality to create a customized risk profile for the clients organization that serves to guide strategic remediation decisions. Learn more about threat landscape and how you can shine a light on the most critical vulnerabilities.
Pinpoint At-Risk Assets with Network Map
Network Map is ideal for visual learners. It allows users to visualize their network security posture by overlaying threat intelligence with vulnerability risk and lets them focus on the most relevant regions of the map. Users can drill into various aspects of the map to view granular information with handy sort and filter capabilities; build high-level or detailed reports based on their Network Map views; and drag and drop clusters to examine connections between assets and threats.
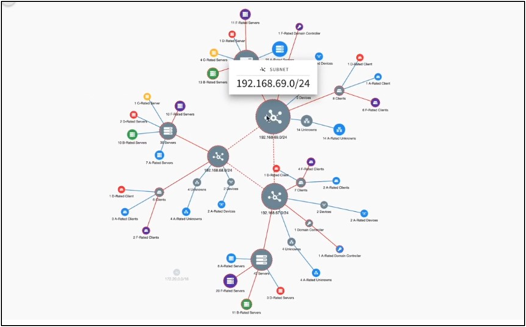
All of this helps users get a clearer, fuller picture of their network. Now you can analyze relationships between assets and threats in ways you never could before. Read the Network Map blog to see how you can get the full picture for better prioritization.
Improve Compliance with CIS Benchmark Scanning
Last but not least is the Center for Internet Security (CIS) Benchmark Scanning feature.
According to CIS Security, CIS Benchmarks are best practices for the secure configuration of a target system. CIS Benchmark Scanning is run using similar credentials to authenticated scanning and includes more than 25 of the commonly used CIS Benchmarks for operating systems and server software.
Its benefits include, but are not limited to:
- Ensuring configurations are in line with industry best practices
- Identifying and resolving configuration settings that are not secure
- Observing standards of regulatory compliance, such as PCI DDS, HIPAA, and NIST
- Protecting your organizations from damaging and costly breaches
Innovative Cybersecurity Solutions for Evolving Client Needs
Client needs always drive our design at Digital Defense, and with the release of the above features for Frontline.Cloud, we’ve made our platform even better. These features allow clients to access new capabilities, analyze trends in insightful ways, and maximize their use of innovative, expert perspectives on network security and risk.
These new, free features make for powerful additions to an already comprehensive platform, rounding it out further and enabling its use as an all-encompassing solution. They are also key components of effective risk-based vulnerability management, the cornerstone for any cybersecurity program.
Not a client yet? Take advantage of our 14-day free trial and discover how the Frontline.Cloud platform makes vulnerability management and threat assessment much easier, more accurate, and more efficient than any other solution.

