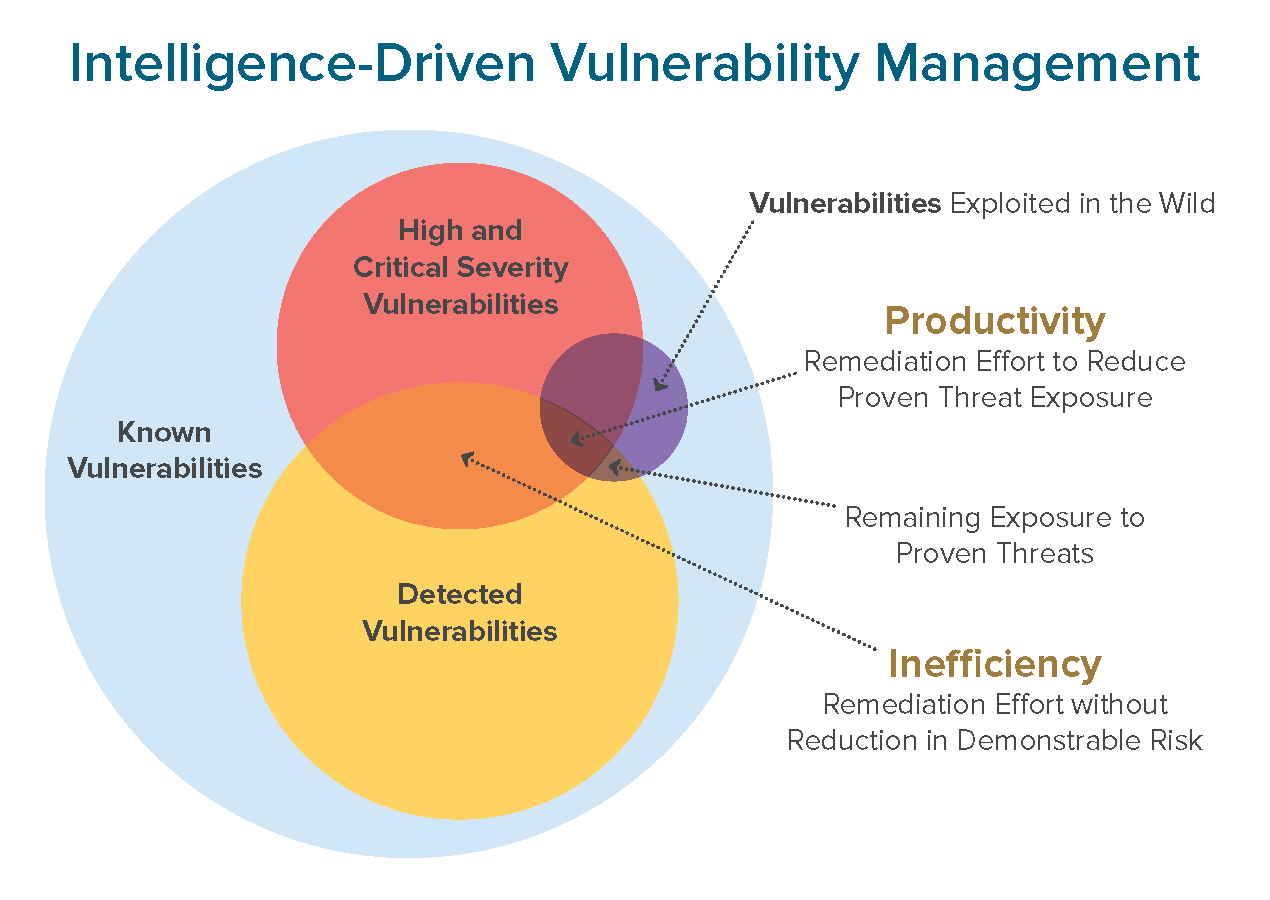
Intelligence-Driven Vulnerability Management
Resource-strapped IT departments need to prioritize vulnerabilities and threats that will have the most impact within their organization's environment. Many businesses rely on common vulnerability and severity metrics (CVE, CVSS, CWE, etc.) to prioritize vulnerabilities that need attention. Attackers, on the other hand, don't necessarily prioritize their exploits by severity scores; they are motivated by the information and tools that are readily available to them.
Your team could have several vulnerabilities scored as critical, but the possibility of exploitation may be low for your environment. Since most organizations have limited resources, time, and skillsets, it's not likely you have an analyst on staff to analyze threat scores and then research the risk of exploitability within your environment.
Providing Context with Threat Intelligence
At Digital Defense we created Threat Landscape in our SaaS cloud-based vulnerability management platform. Threat Landscape leverages threat intelligence to help you understand the truly exploitable vulnerabilities that exist in your environment.
Using our proprietary machine learning model, we combine data from the standard scoring systems with daily threat intelligence feeds and chatter from the dark web, hacker forums, and other intelligence sources to provide curated threat intel relevant to your environment. We feed the data into machine-learning models that rank the possibility of exploitation of assets and vulnerabilities in the context of your organization’s infrastructure.
Threat Landscape allows you to take the leap from awareness of the vulnerability risk in your infrastructure to establishing and tracking an effective remediation strategy so you work smarter rather than constantly working harder.
Exclusive to Threat Landscape are a host of different dashboards that provide insight into active vulnerability threat risk on your network. The Threat Summary dashboard includes an active threat feed of vulnerabilities on your network that have been exploited in the last 90 days along with ratios describing threat activity in the context of your network and overall activity in the wild.
Threat Rank
Threat Rank is the first of two components that make up Threat Landscape.
Threat Rank does what it says. It ranks threats that are exploitable inside your network. Your team gets insight into the likelihood of whether an asset can be compromised. Threat Rank weighs popularity of the vulnerability in the wild, its exploitability, and whether a rootkit for that vulnerability is for sale on the dark web. If all of these conditions exist, the threat is ranked as high, and your team can make a prioritization call.
Threat Rank has several reports that provide clear, comprehensive results. Below is a short list:
- Threat Rank by Asset
- Trending Threat Rank Score
- Outstanding Vulnerability by Threat Rank
- Vulnerabilities You Should Fix
- Threat Rank Breakdown
Threat Rank is now live and accessed from Active View dashboard.
Active Risk Score
The second component of Threat Landscape is Active Risk Score which helps you tune your organization's appetite for risk. We realize there are a myriad of ways to assess risk inside your organization, making it difficult to determine your business's risk threshold. Active Risk Score considers factors unique to your environment using prebuilt or configurable risk profiles combining vulnerability severity, Threat Rank, asset exposure, and asset criticality to create and rate your organization's risk appetite.
Preliminary reporting for Active Risk Score includes:
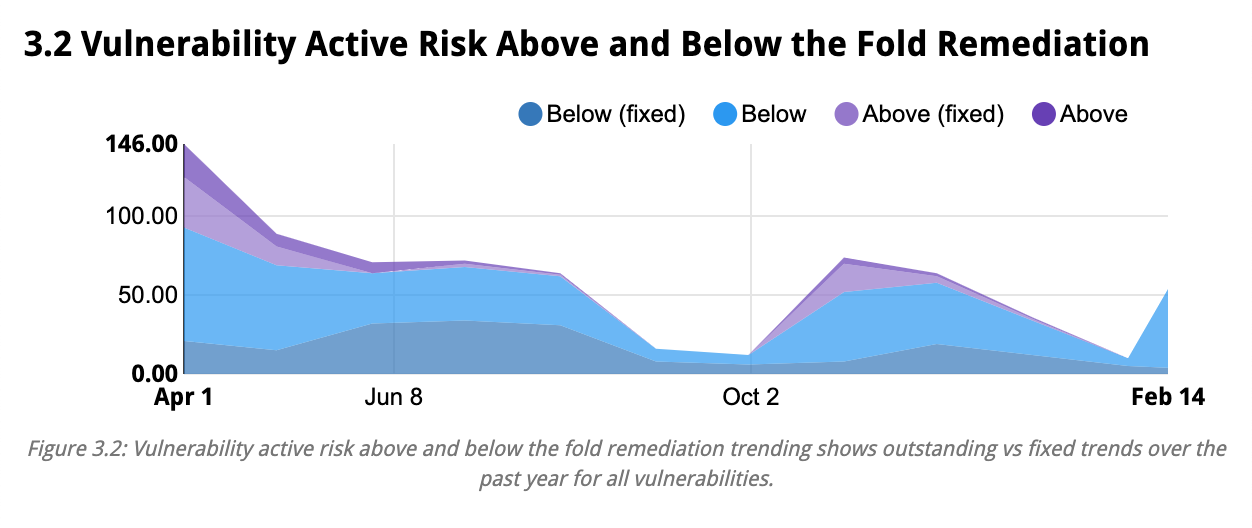
- Vulnerability Active Risk Trends
- Outstanding vs. Fixed by Active Risk
- Active Risks Summary
- Vulnerability Average Age by Active Risk
Watch for our announcement of Active Risk Score in the third quarter.
In Conclusion
Threat Landscape operationalizes Vulnerability Threat Intelligence so you not only curate a remediation strategy that is most productive for your risk posture, but also track and assess the effectiveness of your strategy over time.
This provides better insight into how tuning your remediation plan affects your risk exposure.
Vulnerability Management Made Easy
We're here to simplify and streamline your vulnerability management. Our team is dedicated to ensuring our Fortra VM customers get actionable results and empowering insight in a user-friendly solution. Fortra VM is delivered via our SaaS cloud-based platform that is lightweight and simple to deploy. It also supports our threat scanning (ATS) and web application scanning (WAS) systems. See how Fortra VM can optimize your team's efficiency and impact on overall security posture.
Get a Customized VM Quote
In the cybersecurity industry, one size doesn't fit all. See which level of security coverage you need and get a quote based on your organization and industry.