Healthcare Use Case
Healthcare
Community Healthcare Provider Gains Added PHI Security, Improved Vulnerability Management on a Limited Budget
Learn how a leading community healthcare provider used Fortra Vulnerability Manager (formerly Frontline VM™), a cloud-based SaaS platform, to help ensure better security of Protected Health Information (PHI) for HIPAA and HITECH compliance. The client was able to improve its overall security posture and establish powerful vulnerability and threat management capabilities while operating within existing resource constraints.
The Challenge
Faced with the healthcare industry’s rigorous compliance requirements and the rising risks of cyber attack, the client needed an effective, affordable way to manage vulnerabilities, threats, and their remediation efforts.
Solution requirements included:
- Ease of Use - Due to the client’s limited IT resources, ease of use was essential for their system of choice. The client did not have the IT bandwidth to handle an overly complicated, high-maintenance system. They also needed a solution that would be simple to install and easy to maintain.
- Cost effectiveness - As with many community healthcare organizations, the client was operating on a very limited budget. Therefore, their chosen solution needed to be powerful and scalable, yet cost effective.
- Actionable Results - The client also needed fast, accurate results that would be clearly represented and actionable. Their small IT team could not afford to burn time and resources sifting through complicated, disorganized vulnerability scanning results.
- Proven ROI - The organization required any expenditure on this effort to have a proven return-on-investment and demonstrated cost effectiveness over time.
Results
The client has experienced several benefits of using Fortra VM and was able to meet all of the previously stated requirements.
Benefits include:
- Reduced Risk Through Improved Security GPA®
- In less than 6 months, the client’s Security GPA improved nearly 35%. Security GPA is a rating of security posture that reflects business risk and improvements made to the security of the client’s networks over time.
- Improved ROI and Reduced Total Cost of Ownership
- Cloud-based Fortra VM – The system requires no hardware or software purchases and no license fees. The client’s savings can be demonstrated in terms of total cost of ownership (TCO) and return on investment (ROI).
- Low Maintenance – Because Fortra VM is low maintenance and easy to use, the client has freedom from the day-to-day oversight of its security program. Therefore, the client does not need dedicated IT resources to maintain the system.
- Workflow Management – The client’s PSA manages the end-to-end service delivery that includes customized reporting of assessment and remediation efforts. In addition, the client can view progress through an intuitive online dashboard, Active View. The PSA can respond quickly to any enterprise-wide issues.
- Best-in-Class Expertise –Digital Defense’s Vulnerability Research Team (VRT) proactively analyzes aggregate data to accelerate the discovery of flaws, then analyzes these flaws for rapid identification of Zero Day vulnerabilities, further bolstering security.
- Reduced Scan Times –Digital Defense’s patented NIRV Scanning Engine has reduced the client’s scan times by almost 80%. This allows the PSA to respond quickly to any enterprise-wide security threat the client may encounter.
Return on Investment
The ROI of an information and network security program designed to identify and mitigate risk is measured in reducing its risk of a data breach. The cost of a Fortra VM subscription service is a very small expense when compared to the potential cost of a breach. The ROI for the client is based on the following assumptions:
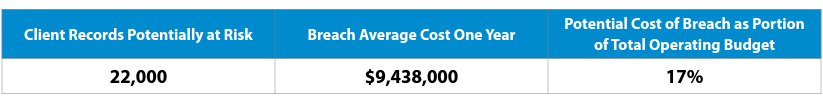
- The client serves approximately 22,000 patients each year, whose records are potentially at risk
- Cost of data breach is $429 per record*
- One data breach could potentially compromise the personal and protected information of their 22,000 patients
- The client’s annual budget is $57 million
The table below shows a potential cost of a data breach of all their patient records if one should occur
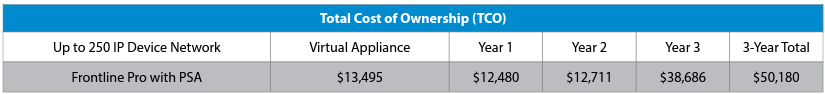
Total Cost of Ownership (TCO)
Based TCO takes into account computer and hardware programs and operational expenses. This client’s network is in the <250 IP device size.
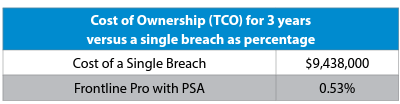
The total cost of a subscription amounts to less than 1% of what a system breach could cost the client, which is a staggering $9.4 million.
The numbers prove that the client has chosen a solution for which the benefits far outweigh the investment. By using Fortra VM, the client is not only experiencing positive ROI, but improved peace of mind when it comes to their security posture.
Solution
The client selected vulnerability scanning and threat management solution, Fortra VM. This cloud-based, SaaS platform is used to conduct host discovery and vulnerability scans on external (internet facing) and internal IP-based systems and networks. It uses patented, proprietary scanning techniques to survey the security posture of the target IP-based systems and networks.
These scans proactively test for known vulnerabilities and the existence of mainstream industry best-practice security configurations.
Other Fortra VM features include:
- Workflow management
- Host-based risk assignments
- Ranking and peer comparisons
- Remediation progress reporting
The client chose a subscription that includes professional, dedicated assistance with configuring and maintaining scan profiles as well as project management of the client’s remediation efforts (regardless of whether they are handled by the client’s IT staff or a 3rd party provider).
Additionally, as a Fortra VM customer, the client was assigned a Personal Security Analyst (PSA) who serves as the primary point of contact for more involved, technical questions. The PSA provides the client with clear, consistent security consulting advice on their vulnerability lifecycle management program.
Copyright © Fortra, LLC and its group of companies. Fortra™, the Fortra™ logos, and other identified marks are proprietary trademarks of Fortra, LLC. | Privacy Policy | Cookie Policy | Sitemap

