P.F. Chang’s recently posted an update on the security breach it had experienced back in June. This update is found at the following link: https://www.pfchangs.com/security/
In this blog post, I spend some time covering the timeline of events and share some thoughts on a cool discovery technique we as Information Generals can use to help us more quickly discover these types of data breaches.
How did P.F. Chang’s discover it had been breached?
Back on June 13th 2014, P.F. Chang’s publicly announced it had fallen victim to an information security breach. Just as in most breaches, this is an instance where the actual cyber security victim, P.F. Chang’s in this case, was unaware of the breach; they were informed of it by an external party. It was actually the United States Secret Service who notified P.F. Chang’s on June 10th that it had been breached. But what tipped them off? If you are like me, you want to understand how we can discover we’ve been breached and the faster we find out, the better.
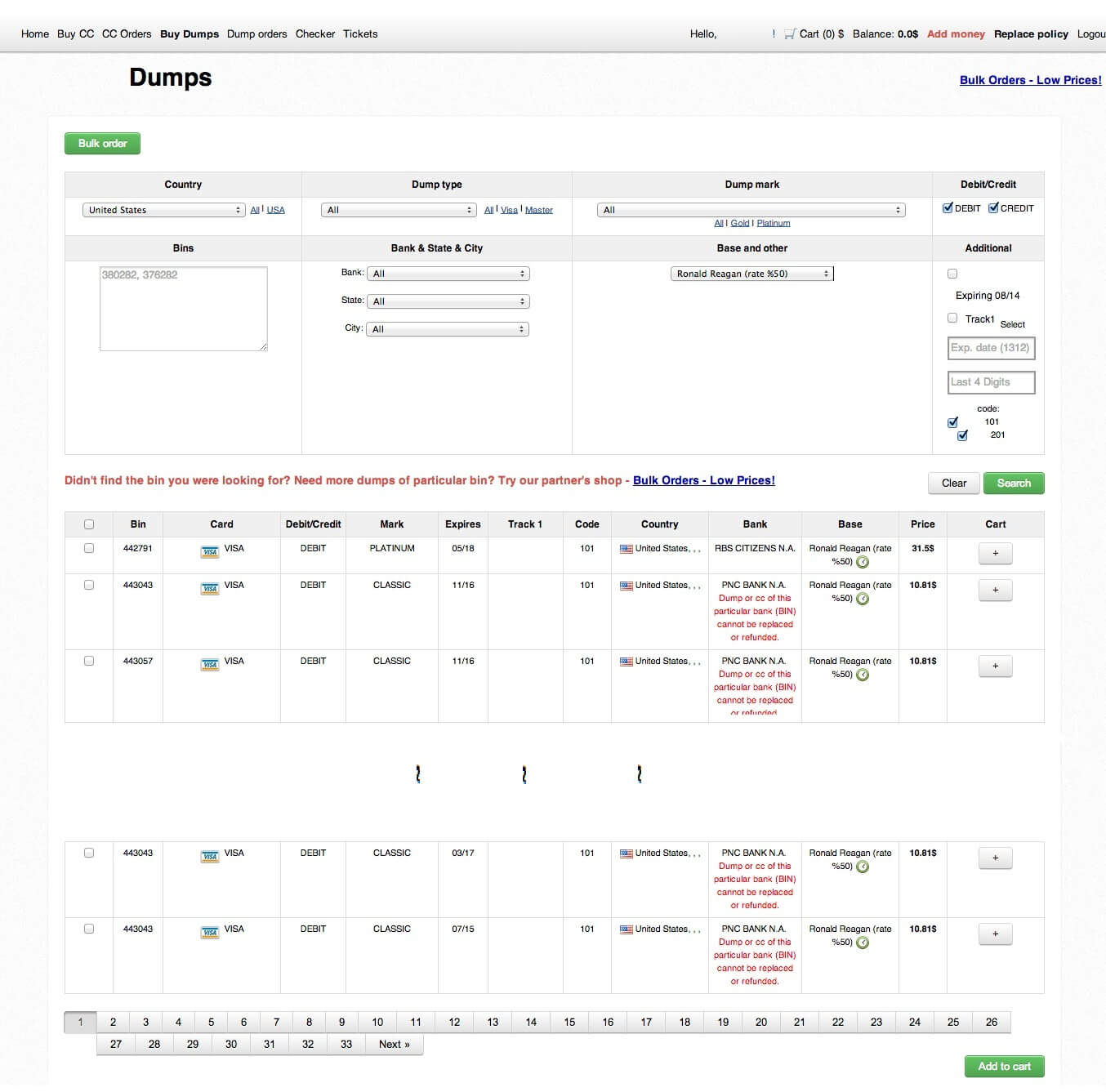
What I find interesting is on June 10th, prior to P.F. Chang’s announcement of this data breach, Brian Krebs of KrebsOnSecurity.com posted a blog entry which you can find here and which raised the strong possibility P.F. Chang’s had been breached. In that blog, Krebs mentions he had been working with several banks on an analysis of a newly posted information set of stolen credit cards which was posted to an underground internet store located at www.rescator.so. This new set of stolen credit card information had just been posted on June 9th with code name “Ronald Reagan.” Let me say that this site was also the same store known for selling tens of millions of cards stolen in the Target Breach.
I went to www.rescator.so site, registered and poked around a little. This is an interesting business and they even track the “valid rate” of their cards which essentially estimates whether or not a given stolen card will work once purchased. The site still has most cards up for sale but the validity rate of these cards has been dropping since the event became known publicly and is now estimated at 75%. It was originally estimated at 100% valid at the time of Krebs blog entry. Because validity has dropped, rescator.so is selling these cards at 50% off. This underground stuff appears organized and it seems to follow supply and demand economics but I digress. To satiate your curiosity, I took a screenshot of my logged in session on this underground site and I share this below.
To continue the story, the banks Krebs was working with, purchased several of the stolen cards which they themselves had issued, so as to obtain the cards’ full credit card numbers. They were then in a position to look up the transactions for these cards and correlate these transactions to determine if there was some company vendor common to the cards’ purchases. They indeed found a strong correlation pointing to a common vendor; you guessed it: P.F. Chang’s!
I share this not because I am promoting illegal activity. I share this because as an information General, I might use this site, along with similar sites, as data feeds into my information defense security analytics with the goal of discovering these types of breaches more rapidly. This is exactly what some financial institutions are doing because they have good Generals on staff. It’s because of this proactive monitoring technique that the P.F. Chang’s breech was discovered.
What information was stolen?
Getting back to specifics of the breech, investigation found that credit and debit card information, issued by various financial institutions and which was used at P.F. Chang’s locations, was compromised. Of course this was evident once correlation of the transactions from various different cards was completed. This information compromised includes credit card numbers, the associated name as well as expiration dates. In short, whatever you need from a credit card in order to purchase something.
When did the breach actually start?
Per the recent information posted by P.F. Chang’s, the data exfiltration started October 2013. However, as posted on KrebsOnSecurity blog titled “P.F. Chang’s Breach Likely Began in Sept. 2013” https://krebsonsecurity.com/tag/p-f-changs-breach/, Visa had issued an alert on June 17th to one of the banks Krebs had been working with related to this issue in which it states “many hundreds of cards exposed in a recent breach that dated back to Sept. 18, 2013.” Therefore it appears Krebs and the banks’ findings of September 2013, is the actual starting point of data exfiltration per our updated knowledge.
P.F. Chang’s Update Posted on their Website
In a responsible move, P.F. Chang’s posted an update on this incident to their corporate website just days ago on August 4th https://www.pfchangs.com/security/. The post includes a reassuring introduction by Rick Federico CEO OF P.F. Chang’s. Within this post, we learn that 33 of P.F. Chang’s restaurants’ credit/debit automated processing systems were compromised and for each location, date ranges are provided. The company also indicates it is providing 1 year of identity theft protection for customers for whom their information was stolen.
Closing Thoughts
All data breaches are unfortunate events. However, I often view events such as these as opportunities to learn and improve my defenses. In exploring this data breach and understanding how it was discovered, we learn we may be able to look for signs out there in the world related to our information and which may point to a data breach which has already occurred, but where hopefully, the data had not yet been used. Although it is possible some of these stolen cards have already been used, it appears that as soon as the information was posted on the www.rescator.so site, banks consumed this information themselves as part of their defense strategy, most likely after learning lessons from the Target breach. In consuming this data feed, credit card issuing financial institutions were proactive in discovering where their information was, even when it was in the wrong hands.
I personally am left with a lingering thought: where does the defense boundary of my information reside? Is the boundary my network perimeter? Does it include my network perimeter, my information hosted in the cloud and also on my employee BYOD devices? Or perhaps this defense boundary part of the very information I am protecting, somehow interleaved in there?
See Firsthand How VM Can Work For You
Request a customized demo and see which cybersecurity vulnerability management options your organization needs.