Offensive Security Bundles for Proactive Cybersecurity
Combine vulnerability management, penetration testing, and red teaming
Our modern threat landscape is constantly evolving and a proactive approach must now be as central to any security strategy as defensive tactics. Reactive controls will always be a necessity, but organizations can also work to reduce the attack surface by anticipating a breach and detecting and responding to security weaknesses before they are exploited.
Get ahead of attackers with the help of offensive security solutions that identify and prioritize risk, provide actionable insights and create an accelerated pathway to remediation. Our offensive security bundles streamline multiple layers of complexity to create a mature security program and ensure your organization can prevent successful cyberattacks.
Anticipate Attacks with Offensive Security Solutions
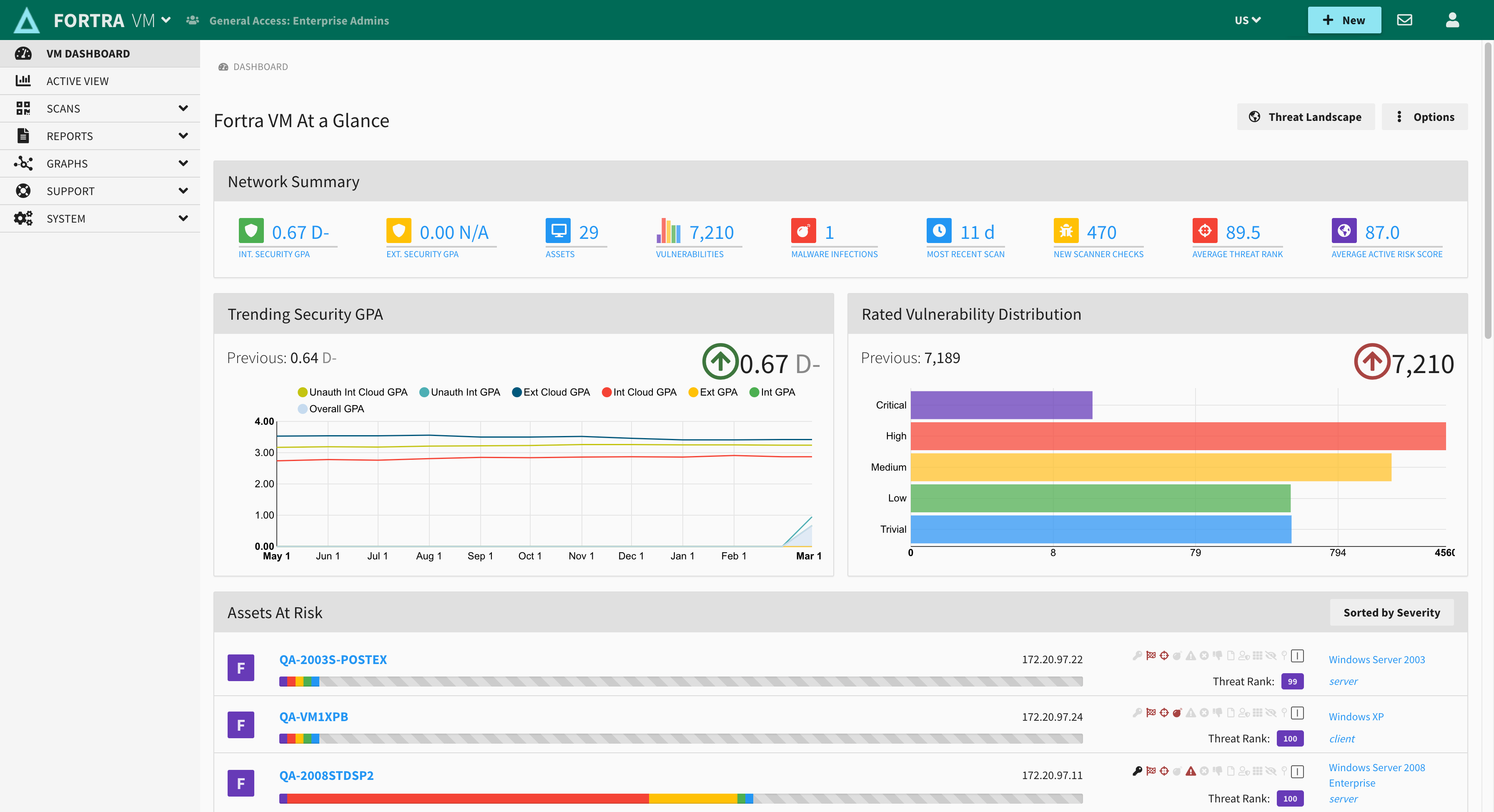
Vulnerability Management with Fortra VM
With proprietary scanning technology and threat intelligence, Fortra VM is a SaaS vulnerability management tool that performs superior network security assessments. Choose one of the many robust built-in scanning options, or tailor one to your own environment using the multiple filtering options. The actionable results can not only be easily tracked and managed within the tool, they can also be used to generate informative reports to fulfill and prove compliance to numerous industry regulations. Fortra VM is known for its ease of use and exceptional customer support that helps IT teams work more efficiently and effectively.
Penetration Testing with Core Impact
This powerful penetration testing tool allows you to safely test your environment using the same techniques as today's attackers. Users can run advanced pen tests with ease using guided automations, certified exploits, and multi-vector testing capabilities. With this centralized toolset, security teams can efficiently discover, test, and report all in one place. Core Impact also offers a ransomware simulator designed to test an organization’s ability to fend off a ransomware attack.

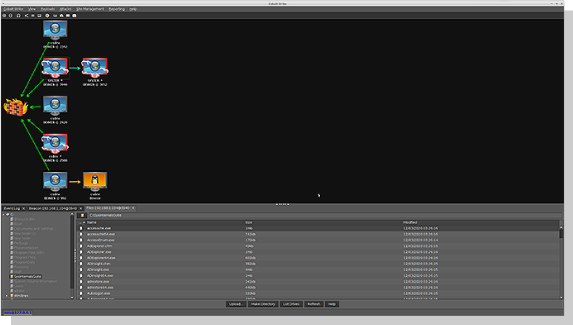
Red Teaming with Cobalt Strike
This robust threat emulation tool provides a post-exploitation agent and covert channels ideal for Adversary Simulations and Red Team exercises. Replicate the tactics and techniques of a persistent embedded threat actor in an IT network, staying covert with malleable C2 that allows you to change your network indicators to look like different malware each time. Additionally, a flexible framework allows users to extend Cobalt Strike’s capabilities by making changes to built-in scripts or bringing their own weaponization.
Layering Security Solutions For Full Coverage

Interoperability and Integrations
These three solutions not only work in tandem, those with the Elite Bundle can also take advantage of how they work together. By importing Fortra VM’s intelligent vulnerability scans, Core Impact can swiftly validate vulnerabilities and utilize the data for other pen tests. Core Impact is also interoperable with Cobalt Strike, and can utilize session passing, tunneling, and shared modules to extend testing capabilities.

Bundle Solutions for Maximum Coverage
With the Offensive Security bundles, you can assemble your proactive security portfolio all in one place, choosing the combination that best fits the needs and security stance of your organization. Each one of our bundle offerings provides centralization and reduced console fatigue that will enhance and accelerate your security. Choosing an Offensive Security Bundle doesn’t just mature your security at a discounted price. By consolidating vendors, you’ll also benefit from the efficiency of having the same best-in-class sales and technical support that Fortra offers across solutions.
Essentials Bundle |
Advanced Bundle |
Elite Bundle |
| Fortra VM & Core Impact | Core Impact & Cobalt Strike | Fortra VM, Core Impact, & Cobalt Strike |
|
|
|
| GET A QUOTE | GET A QUOTE | GET A QUOTE |
Featured Resources
Need help figuring out which bundle is right for you?
Let us know about your needs and security goals and our security experts will help determine which bundle is the right fit for your organization.
Copyright © Fortra, LLC and its group of companies. Fortra™, the Fortra™ logos, and other identified marks are proprietary trademarks of Fortra, LLC. | Privacy Policy | Cookie Policy | Sitemap

