As a response to the COVID-19 (novel Coronavirus) outbreak, many companies are enacting Work-From-Home (WFH) policies for their employees. Organizations are quickly realizing that the bulk of their business-critical operations and communications must be performed remotely. While businesses initially began mandated WFH policies thinking they would last about two weeks, it’s beginning to look like they may have to continue into the summer. This extended period, coupled with the changing infrastructure and support requirements, is creating a technical challenge that must be met quickly, effectively, and securely.
Straining the Corporate Network
While many organizational infrastructures support some remote worker capabilities, they are not generally built to handle the security workloads and management of an entire company for an extended period. Core operations are suddenly sitting outside of traditional perimeters. IT teams are straining to properly manage and secure a profusion of BYOD assets, all of which are running across traditional ISPs.
Highly regulated industries face additional compliance challenges presented by the proliferation of remote work. Banking, insurance, legal, and especially healthcare organizations are not generally set up for extended remote work and the related need to access and share highly regulated and sensitive data remotely. These organizations are scrambling to expand their remote system access and management while adequately protecting sensitive information from malicious actors.
Attackers Are Already Exploiting the Situation
Cybercriminals and nation states have already started to leverage the global anxiety around the coronavirus outbreak for their benefit. They are targeting distracted organizations with phishing and ransomware attacks while also looking at ways to exploit the dramatic and sudden increase in remote workers and strained corporate networks. Forbes shared some recent examples of attackers using COVID-19-related phishing emails to install malware on systems. These phishing attacks take advantage of a Microsoft Windows vulnerability that many organizations may be too distracted to patch. Threat actors have also begun using ransomware against victims they infect with the AZORult and Emotet varieties of malware, a tactic that has been employed effectively during other times of crisis.
Exposed Non-Corporate Remote Assets
As a first line of defense, it is critical to assess the risk posture of BYOD devices or systems running on home networks before opening them to corporate networks. With mixed usage for personal and work related-activities, home networks are open to more attacks. They often lack adequate protection or operate minimal security controls and monitoring such as:
- Network firewalls
- Intrusion prevention
- URL filtering
- Web Application Firewall (WAF)
- Endpoint Detection and Response (EDR)
Additionally, security patching of these personal systems is generally executed ad-hoc, if at all, as they are not part of a corporate security program.
As remote work suddenly and rapidly expands, organizations are struggling to secure and manage an exponentially larger attack surface. Fundamentally, managing and tracking assets just got significantly harder.
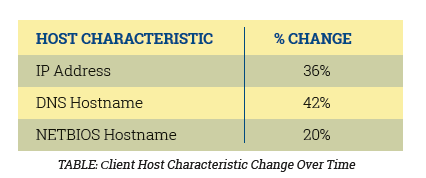
Case in point, an IP address or other identifying information for remote workers can change from day-to-day if not more frequently. This makes resources hard to identify and monitor for security risks and hinders security policy enforcement.
A Unique Agentless Real-Time Approach
Determining asset risk and taking steps to alleviate that risk is core to preventing a potentially compromised system from penetrating a corporate network. Most vulnerability management or endpoint solutions require an agent to be installed, but that is not an option in this scenario. So how does a company assess and secure the increasingly dynamic set of assets that are now remote or across the cloud?
Organizations must use an agentless security solution that can assess each asset quickly, identifying potential vulnerabilities as well as existing malware that has already infiltrated. The right solution can do this with minimal performance impact. As organizations continue to see the proliferation of BYOD, they must also utilize on-demand scanning. Their security landscape is changing at an unprecedented pace, so repeated vulnerability scanning is necessary to stay secure and compliant.
Digital Defense provides agentless vulnerability management and threat assessment Software-as-a-Service (SaaS) solutions and services. They are purpose-built to operate in hybrid cloud environments including assessment of remote and BYOD assets without the need to run agents.
During this period of adjustment for so many organizations, we encourage the use of our Frontline.Cloud™ solutions free for 30 days to help assess rapidly changing networks. Following the completion of the trial, a 30-day extension can be granted upon request. Our solutions are quick to stand up and simple to use, so organizations and IT teams of any size can benefit. Click here to get started.
About Digital Defense Solutions
Our Frontline.Cloud platform supports Frontline Vulnerability Manager™, Frontline Web Application Scanning™, and Frontline Active Threat Sweep™ that together provide agent-less discovery, asset tracking, OS and web application risk assessment, and targeted malware threat assessment of today’s dynamic assets. The Frontline.Cloud platform virtually eliminates false-positives associated with legacy vulnerability management solutions, while also automating the tracking of dynamic and transient assets and prioritizing results based on business criticality. Learn more.
See Firsthand How VM Can Work For You
Request a customized demo and see which cybersecurity vulnerability management options your organization needs.